LARAVEL SMTP CRACK | HOST: or how to have a nasty day
If you are reading this, it may be because your SMTP credentials have been abused, raped and shot dead by the pesky hackers. And you are worried that your Laravel app is insecure.
Not long ago, we were in the same situation.
Don’t worry, Laravel is not insecure.
But the human factor is to be taken into account.
Our story is simple: a sandbox account was compromised by what looked like a targeted attack. The SMTP credentials have been extracted and used by some unknown entity to fill the victim’s spam boxes with fake Viagra ads*.
We went into panic mode and tried to figure out wtf happened.
As it turned out, the reason was really simple: our Laravel instance had the APP_DEBUG set to true: simply put, an "ooops" error will expose the env content.
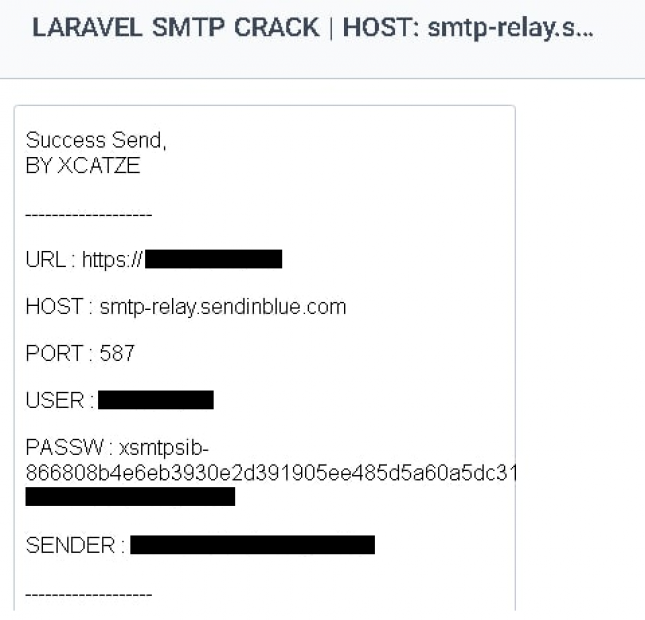
But there is more to that: looking at the initial test email from the SMTP logs, we realized there’s got to be some tool out there that does this.
The keyword was “xCATZE” and we were able to find some movies on YT, where the tool can be seen in action.
A bit more research later we could safely say that the tool is based on a python script, in many incarnations and versions, that targets Laravel systems specifically and uses several ways to attack the host by:
- generating an "oops" error (a simple POST request with no parameters to the website causes it)
- trying to get the .env file from several known routes
- attempting to inject a shell using a known security fault via the Ignition package
We were able to source the tool and we can say it has more features such as doing reverse IP, getting a list of Laravel sites using google dorks and other naughty things.
Conclusion
Q: What you can do?
A: NEVER have the production Laravel website in APP_DEBUG=true mode.
Or any public Laravel instance, if the credentials to be exposed are critical
Note: if you *really* need to have the debug mode enabled for some (lazy) reason then you could at least:
-use the debug_blacklist option in your config/app.php
-password protect the website directory
Relevant links:
https://www.mailgun.com/blog/a-word-of-caution-for-laravel-developers/
https://www.ambionics.io/blog/laravel-debug-rce
https://stackoverflow.com/questions/46407009/how-to-hide-env-passwords-in-laravel-whoops-output
____________________
* It was far worse, but we wouldn't say what